RFP Risk Management: Physical and digital risk management strategies are worlds apart, yet their failures can be equally devastating. Take construction site safety and patient data protection in Request for Proposal (RFP) processes. Construction risks can cause immediate physical harm, while breaches in patient data can destroy privacy and leave lasting scars.
Healthcare organizations must protect digital information that flows nonstop through their systems. Construction sites also need strict safety protocols to keep workers safe from falls, faulty equipment, and environmental dangers. Companies then have to tackle both physical and digital threats in their risk management approach, especially as they assess vendor capabilities through RFPs. Risk assessment models in both construction and healthcare share basic principles – they identify, assess, and reduce risks.
This piece dives into RFP risk management strategies that work in both worlds, their differences, and where they overlap. We’ll also learn about the rules each sector must follow – from OSHA guidelines at construction sites to HIPAA requirements for patient data. Understanding these two different risk landscapes will help create stronger evaluation criteria for RFPs across industries.
Understanding Risk Domains in RFPs
Image Source: SlideKit
RFP documents help identify and manage potential risks in different industries. These documents must deal with specific risks that could affect project success, compliance, and safety. Organizations can develop better RFP risk management strategies when they understand these distinct risk areas.
Construction Site Risk Categories in Public Projects
Public construction projects face unique physical, financial, operational, and environmental risks. Health and safety risks are the main concerns in construction RFPs. Worker accidents, equipment failures, and exposure to dangerous materials can threaten worker safety. Construction RFPs ask bidders to show OSHA standards implementation and safety protocols to handle these issues.
Project delays and cost overruns pose another major risk to construction projects. Even well-planned projects can go off track due to material shortages, labor disputes, weather issues, and design changes. RFPs must assess bidders’ risk-based scheduling tools, contingency plans, and budget management approaches.
The construction process needs to focus on several risk areas:
- Site access and security – Proper controls to stop unauthorized entry and protect equipment
- Environmental hazards – Control of potential contamination, pollution, or ecological damage
- Structural integrity – Proving design meets building codes and safety standards
- Utility disruptions – Plans to handle interruptions to water, power, or other vital services
Construction RFPs must also handle compliance risks. Industry experts say that “failing to identify and manage a potential project risk is basically accepting the risk should it present itself during your project”. RFPs need to assess how well bidders understand building codes, environmental regulations, and safety standards.
Patient Data Risk Categories in Healthcare RFPs
Healthcare organizations deal with different risks that focus on sensitive information and patient safety. These organizations are more vulnerable to cyber attacks than other sectors. The consequences of security breaches are much worse. The HHS’ Office for Civil Rights reported 66 data breaches with 500 or more records in April 2025 alone.
Patient data RFPs need to protect against several key risks. System vulnerabilities could disrupt core operations and delay patient care. Financial risks include threats to an organization’s stability from sudden costs or legal fines after data breaches or compliance failures.
Healthcare providers don’t deal very well with compliance risks. They must guide through complex regulations including HIPAA privacy and security requirements. Healthcare RFPs must prioritize compliance risk management.
Third-party risks are vital for healthcare RFPs to address. Organizations work with many external vendors, from cloud service providers to billing companies. These vendors often have access to sensitive healthcare data. A complete healthcare risk strategy must monitor these partners’ operational, ethical, and compliance risks.
RFPs are vital tools that make risk mitigation a project priority in both sectors. Organizations can exclude vendors who don’t share their risk management approach by outlining risk areas and asking for detailed mitigation strategies. This protects projects, patients, and public interests.
Comparing Risk Profiles: Physical vs Digital
Physical and digital risk landscapes create unique challenges for organizations as they develop detailed RFP risk management strategies. Physical risks show immediate, visible effects. Digital risks can hide undetected until they cause major damage. This basic difference determines how companies assess, prioritize, and alleviate risks in different sectors.
On-site Hazards and Construction Safety Management
Construction remains one of the most dangerous occupations based on alarming safety statistics. European construction sites reported 3,332 deaths in 2018, which made up one-fifth of all fatal workplace accidents. The numbers look worse in the United States. Construction workers suffered 1,061 deaths out of 5,333 total workplace fatalities in 2019. The death rate in construction is four times higher than other industries.
Workers face many deadly hazards each day, including:
- Falls from heights (framework, ladders, unprotected edges)
- Struck-by incidents involving falling objects, vehicles, or machinery
- Caught-in/between hazards where workers become trapped by equipment
- Electrical hazards from live wires and faulty equipment
- Exposure to hazardous materials and dangerous atmospheres
Traditional safety methods don’t work very well anymore. Companies now welcome digital technologies for risk management. Building Information Modeling (BIM) creates virtual construction site models. These simulate activities like crane movements and worker positions to spot potential dangers. Teams can identify risks such as cranes moving over work areas and take preventive steps before work starts.
Digital twin technology provides more advanced monitoring through sensors and wearable devices. These detect unsafe worker movements, fatigue, or when workers get too close to dangerous areas in real-time. Small and medium-sized construction companies still face challenges with costs and accessibility.
Data Breach Vectors in Healthcare IT Systems
Healthcare faces a completely different risk profile focused on protecting sensitive patient information. The Ponemon Institute reports that healthcare data breaches cost $7.13 million per incident, the highest across all sectors. Each compromised healthcare record costs $146, rising to $150 when personal health information (PHI) gets exposed.
A study of 1,485 breach events between 2015 and 2020 showed unexpected patterns in healthcare data vulnerabilities. In stark comparison to this common belief, unintentional factors caused 73.1% of affected records rather than malicious attacks. Unintentional factors affected 123,446 records on average – more than double the number caused by malicious actions.
Healthcare’s most damaging breach vectors include:
- Phishing scams (221 reported incidents) affected more records than any other method
- Ransomware attacks (119 reported incidents)
- Carelessness and negligence (382 incidents)
- Theft of physical devices containing data (222 incidents)
Financial damage goes beyond breach costs. Healthcare organizations lose about $900,000 daily from ransomware-caused outages, not counting billions paid in ransoms. Security breaches increased by 239% from 2018 to 2023, with ransomware attacks jumping 278%.
Healthcare falls behind other industries in cybersecurity readiness. About 37% of healthcare organizations have no cyberattack response plan. This creates major weaknesses in protecting patient data.
Both sectors show how risk profiles shape management approaches. Construction safety now relies on technological breakthroughs to prevent immediate physical harm. Healthcare must balance technology with human-centered solutions to address unintentional breaches. Risk management strategies must consider each domain’s unique characteristics and evolving threats.
Risk Assessment Methodologies for Each Domain
Image Source: SlideKit
Risk assessment methods are the foundation of successful risk management strategies in different fields. Each domain needs its own specific assessment framework to tackle unique challenges rather than using general approaches.
Construction Risk Assessment Frameworks
Construction risk assessment works in three main phases: identification, estimation, and assessment. Project managers use this organized approach to spot potential hazards before they turn into expensive problems. The complex nature of construction projects has led to several specialized frameworks.
Research that analyzed different assessment methods found ten main frameworks that work well in construction: INSHT, ANACT, THREP, SHERPA, RNUR, EVENT TREE, LEST, FINE, ERGONOMIC ANALYSIS, and PSYCHOSOCIAL FACTORS. Four of these methods—INSHT, ANACT, RNUR, and FINE—have shown they work especially well in construction settings.
Most construction risk frameworks use a simple formula: R = P × I. Here, R shows risk level, P shows how likely something is to happen, and I shows the effect. The result falls between 0 and 1, with higher numbers meaning bigger risks. Some frameworks write this as R = P × C, where C stands for consequences.
Construction projects usually assess probability in two ways:
- Subjective analysis: Experts make direct estimates
- Objective analysis: Past data guides the review
Most frameworks use qualitative or semi-quantitative approaches because construction sites often don’t have enough historical data for objective analysis. Risk effects are also hard to measure since similar accidents can have different levels of severity.
Construction managers need to use several assessment methods at once to protect their projects fully. Studies show that using just one method misses many risks because each framework is better at finding different types of problems. Some methods don’t catch extremely high or low risks well, so using multiple approaches works better.
Healthcare Safety Risk Assessment Models
Healthcare safety risk assessment tools focus on both physical safety and data security. The Safety Risk Assessment Toolkit, created by the Center for Health Design with AHRQ funding, looks at six key safety areas: infections, falls, medication errors, security, behavioral health injuries, and patient handling.
Healthcare models work differently from construction frameworks. They bring together teams of architects, designers, clinicians, pharmacists, risk managers, facility managers, and security staff to review more than 200 environmental factors. This team approach helps find more risks through different expert perspectives.
Healthcare risk matrices are important assessment tools, but traditional ones struggle with uncertainty. New graphical methods now use two-dimensional intervals to show uncertainty in both probability and impact. A study with healthcare professionals found that showing uncertainty through rectangular visuals got different results than regular point-based matrices, especially when estimating probabilities.
Healthcare facilities use risk assessment to improve:
- Workflows that reduce infection spread
- Where to put isolation rooms and sinks
- How to keep clean and dirty materials separate
- Light and noise control to avoid medication mistakes
- Where to place patient handling equipment
The rise of healthcare risk assessment shows a growing understanding that patient safety depends on both facility design and data security. Healthcare risk management needs specific assessment methods that address both these areas’ unique challenges.
Compliance Requirements in RFPs
Regulatory compliance serves as the foundation for managing risks in construction and healthcare. RFPs need clear compliance requirements so vendors can meet complex regulatory rules that protect workers, patients, and sensitive data.
OSHA and Local Building Code Mandates
The OSH Act created OSHA in 1970. Its mission was to develop workplace safety and health standards to reduce accidents from poor working conditions. Construction RFPs must address OSHA compliance because violations can lead to hefty fines – up to $161,323 per incident. The exact amount depends on how serious the violation is, past compliance records, and cooperation during investigations.
Construction RFPs usually need detailed safety protocols covering:
- Personal protective equipment requirements
- Fall prevention systems
- Site condition monitoring
- Emergency response procedures
Local building, fire, noise, and safety codes often have stricter rules than federal or state regulations. To name just one example, Dallas Fire Code (§403.11.1.3) sets higher standards for standby personnel compared to OSHA requirements. New York’s Construction Code (§28.103.21) also requires more detailed injury reporting. Construction RFPs must factor in these location-specific differences.
Building codes set minimum standards to ensure structural safety and protection from hazards like faulty wiring, weak structures, and fire risks. RFPs need to confirm that bidders understand and commit to meeting these requirements during the project.
HIPAA Compliance Requirements for Patient Data
HIPAA changed how healthcare manages risks by creating strict rules for protecting patient information. The law started as health insurance reform but grew to include measures that reduce fraud, simplify healthcare transactions, and protect patient privacy.
HIPAA’s Privacy Rule protects all “individually identifiable health information” that covered entities and their business partners handle or send in any format—electronic, paper, or verbal. This protected health information (PHI) includes:
- Past, present, or future physical/mental health conditions
- Healthcare provision details
- Payment information for healthcare services
- Demographic data that could identify individuals
Healthcare RFPs must spell out vendor responsibilities for PHI. Covered entities need written permission to use or share PHI unless the Privacy Rule specifically allows it. This means RFPs should state regulatory expectations clearly and ask vendors to prove they comply.
The related HIPAA Security and Breach Notification Rules require safeguards for electronic PHI confidentiality, integrity, and availability. They also mandate procedures to alert people when someone improperly accesses their health information. Healthcare RFP workflows must build in these requirements through templates that match current regulations.
Healthcare’s strict regulations mean RFPs must tackle compliance challenges head-on. Organizations can involve compliance experts during vendor evaluation or use systems that ensure proposals meet industry regulations. This approach lowers non-compliance risks and creates transparent procurement.
Both construction and healthcare RFPs must make complex regulations easy to understand. Setting clear standards early helps organizations better assess if vendors can handle compliance risks in physical and digital spaces.
Mitigation Strategies for Construction Site Risks
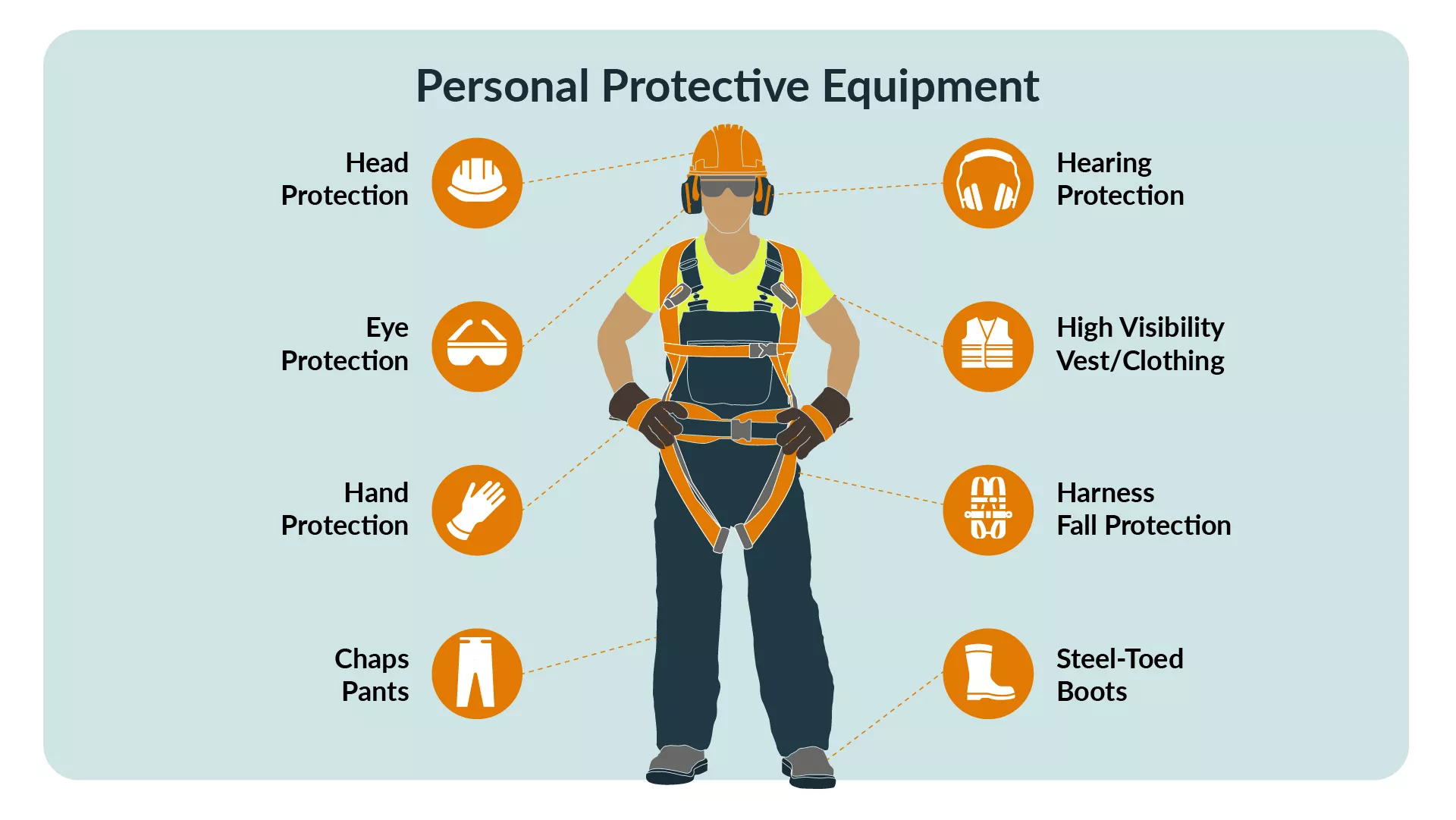
Image Source: AlertMedia
Construction sites face many hazards that need specific strategies to keep workers safe and projects on track. A structured approach to risk management helps address both human and environmental challenges at these sites.
Site Access Control and Worker Safety Protocols
The core team must control who enters and exits potentially dangerous areas at construction sites. Strong perimeter control through fences, gates, and walls provides the first line of defense against unauthorized access. This protection stops theft and vandalism while keeping untrained people away from hazardous zones.
Access management relies heavily on identification systems. These typically include:
- ID badges or digital credentials that verify worker authorization
- Electronic access systems such as key cards or biometric scanners
- Visitor management protocols requiring sign-in and escort procedures
These measures do more than prevent unauthorized access. They create accountability and track everyone present on-site – vital information during emergencies or safety incidents. The quickest way to simplify tracking involves directing all personnel through monitored entry points.
Safety protocols must go beyond access control. Every worker needs proper training to recognize hazards and follow safety procedures during site inductions. Leading safety programs emphasize that workers must “operate machinery properly, consistently wear personal protective equipment (PPE), and maintain a culture of safety on the site”.
Equipment Failure and Environmental Hazard Planning
Construction sites face various environmental hazards from explosions to toxic exposure. Site managers can prevent explosions by maintaining clean work areas through:
- Providing designated trash areas for construction waste and worker-generated garbage
- Establishing smoking areas away from excavations and standard trash areas
- Never allowing burning of trash or refuse on job sites
Toxic substance exposure remains one of the biggest problems. Workers should stop work immediately if they find unidentified chemicals. They must follow Safety Data Sheet instructions for known chemicals and avoid gathering near vehicle exhausts to reduce harmful fume inhalation.
Dust mitigation needs special attention because silica dust causes chronic illness with regular exposure. The team can minimize traffic on dry, disturbed soil, set site speed limits, and use water trucks to keep soil particles grounded. Workers without cabbed vehicles should receive appropriate PPE including respirators, masks, and goggles when dusty conditions persist.
Water creates multiple risks including drowning, electrical shock, hypothermia, and slip injuries. Contractors should ensure proper drainage throughout the site before final grading and use pumps to remove water from pit excavations.
Green practices should guide construction projects through waste management systems that separate waste, recycle materials, and dispose of materials responsibly. The team must plan for unexpected weather, supply chain problems, and economic changes by maintaining emergency reserves.
A well-laid-out Risk Management Plan (RMP) helps alleviate risks across the construction process. This plan identifies potential construction risks, assigns responsible parties, and outlines strategies to address these challenges.
Mitigation Strategies for Patient Data Risks
Image Source: HIPAA Vault
Patient information needs specialized digital protection that works differently from physical security measures. Healthcare organizations now face increasing pressure to protect sensitive data. They need budget-friendly risk management strategies to prevent breaches and follow regulations.
Data Encryption and Access Control Policies
Encryption turns patient data into an unreadable format without the right decryption key. This serves as a basic defense against unauthorized access. The HIPAA Security Rule identifies encryption as an addressable implementation specification. Healthcare organizations must implement it unless they document why it’s not reasonable and adopt equivalent measures. Organizations that follow NIST standards for both data at rest (NIST SP 800-111) and data in transit (NIST SP 800-52) gain extra benefits toward meeting recognized security frameworks.
Data encryption must protect two main states:
- Data at rest protection: Covers information stored on servers, desktop files, USB drives, and mobile devices
- Data in transit security: Protects information as it moves across networks or communication channels
The right implementation goes beyond simple encryption. Healthcare organizations need to strengthen their data security:
- They should apply encryption to as much data as possible. This includes login credentials and authentication codes to create multiple barriers for potential attackers
- Email encryption solutions must protect both text content and file attachments. They need integrity controls to stop unauthorized changes
Access control policies work with encryption to decide who can view or change protected health information. The Security Rule requires covered entities to create technical policies. These policies let only authorized people access electronic protected health information (ePHI). Organizations should set up their EHR systems to give access only to people who need it.
Audit Trails and Role-Based Access in EHR Systems
Audit trails create records of system events that show who accessed data, what they did, and when it happened. The Security Rule requires regulated entities to use hardware, software, and procedural tools. These tools record and track activity in information systems with ePHI. Audit trails play several vital roles in healthcare risk management.
They create accountability by keeping clear records of data access and changes. The trails support access control by spotting unauthorized attempts. Organizations can trace breach sources, understand their scope, and check damage to PHI.
Role-based access control (RBAC) adds another vital security layer. It assigns access rights based on job duties instead of individual identities. Healthcare organizations usually create several access levels:
- Full access for Chief Medical Information Officers and security personnel
- Department-specific access for attending physicians
- Individual case access for nurses and specialists
- Metadata-only access for administrative staff
RBAC works well with audit logging. Research shows that usage patterns from commercial EHR systems can predict certain healthcare system roles accurately. This approach helps reduce management work while maintaining security through automated role prediction and validation.
Vendor Security Evaluation in RFPs
Vendor assessment plays a vital part in healthcare data protection since third-party partners often access sensitive information. Healthcare organizations should look at three key security areas when they review vendors through RFPs:
- Product Security: Making sure vendors create software that’s “secure by design” with security built into development
- Deployment Security: Checking proper installation processes including firewalls, proxies, server hardening, and certificate management
- Operational Security: Ensuring ongoing maintenance for passwords, access privileges, and security patches
RFPs need detailed security questionnaires to check vendor encryption practices, access controls, incident response policies, and compliance with frameworks like HIPAA, GDPR, and SOC 2. Organizations must use these questionnaires throughout the vendor’s lifecycle. They help evaluate potential partners’ risk levels, spot new risks, and check performance during offboarding.
Healthcare organizations that use these layered protection strategies build resilient barriers. These barriers stop both malicious attacks and accidental breaches while keeping patient trust and meeting regulations.
Integrating RFP Risk Management into RFP Evaluation Criteria
RFP processes must include clear criteria to assess how vendors handle risk management. These criteria help determine if potential partners can identify, analyze, and reduce domain-specific risks in both construction and healthcare sectors.
Scoring Risk Mitigation Plans in Construction Bids
Construction RFP assessment relies on quantifiable scoring systems that measure bidders’ risk management skills. The structured procurement process will give a fair evaluation of all proposals and arranges them according to project values while achieving stakeholder needs. Procurement teams usually create a 100-point weighted system that assigns percentage scores to each category.
Construction RFPs should assess these factors along with standard cost considerations:
- Adequacy of competitive bidding documentation and compliance with federal requirements
- Vendor prequalification documentation and past performance metrics
- Inclusion of cost control clauses and milestone payment structures
- Implementation of performance measures and appropriate termination clauses
Successful contractors build risk analysis into their bidding process before submission, which leads to more precise pricing. They start by spotting potential risks such as incomplete construction documents, site conditions, accelerated timelines, safety concerns, delays, change orders, and unexpected material cost increases. Risks with high impact and high probability need primary focus, and their reduction costs should be included in the bid.
Assessing Data Security Provisions in Healthcare Proposals
Healthcare RFPs must thoroughly assess vendors’ data security capabilities due to rising cybersecurity threats. Large data breaches (500+ records) in healthcare organizations jumped 102% in the last five years. The number of affected individuals saw an alarming 1002% increase. Since 2019, hacking incidents grew 89% while ransomware attacks increased by 102%.
Healthcare RFP assessment criteria should examine vendors’ implementation of specific technical measures:
- Mandatory encryption of ePHI both at rest and in transit
- Deployment of multifactor authentication systems
- Network segmentation and consistent technical controls
- Vulnerability scanning (every six months) and penetration testing (annual)
- Anti-malware protection and removal of extraneous software from systems
Healthcare RFPs need proof of incident response capabilities, including plans to restore critical systems within 72 hours after disruption. Vendor assessments must verify annual security audits and written certification from business associates that confirm deployment of required technical safeguards.
These assessment criteria help organizations choose partners who understand domain-specific risks and show real abilities to manage them throughout project implementation.
Cross-Domain Lessons and Shared Best Practices
Physical and digital domains share basic risk management principles even though they deal with different hazards. Teams can build stronger organizational resilience by learning from both domains’ experiences.
Incident Response Planning Across Domains
Good incident response plans work as essential frameworks in construction and healthcare settings. These plans are “written documents, formally approved by senior leadership” that define roles and responsibilities during crises. A complete IRP should assign key positions no matter the field. An Incident Manager coordinates communications, a Technical Manager acts as subject matter expert, and a Communications Manager deals with external stakeholders.
Preparation is the life-blood of good incident management in every sector. Teams should run attack simulation exercises regularly. These “tabletop exercises” let teams act out scenarios like data breaches or construction accidents. Organizations need stakeholder notification plans that list everyone who needs updates during incidents.
Looking back meetings offer great learning chances in both areas. These “blameless” reviews should get into the incident timeline and system failures. Teams can spot improvements without pointing fingers at individuals. Healthcare and construction projects use complex systems, so these reviews should look at how people, processes, and technology played a part in incidents.
Training and Awareness for Risk Reduction
Standard security awareness methods don’t work well enough in physical and digital spaces anymore. Data breaches involve human interaction 70% of the time. Organizations need human risk management strategies that fix behavioral weak spots.
Training and awareness should boost organizational cyber resilience through planned steps: finding needs, building skills, and measuring results. Construction safety needs similar structured approaches to cut down physical risks. Both fields work better when security culture grows beyond just following rules to where “people exhibit the right behaviors even when they are not told what to do”.
Like technical controls, people-focused security needs proper resources and planning. Teams should find passionate communicators who can explain complex ideas in simple terms. Training should connect to real-life applications instead of just checking compliance boxes.
Vendor Accountability and SLA Enforcement
Service Level Agreements create solid accountability frameworks that help construction and healthcare fields. These contracts “specify vendor obligations, usually in quantifiable terms” and cover technical performance, customer service, and other measures.
SLAs create accountability by turning promises into measurable metrics and supporting critical operations. Construction projects now use performance-based agreements more often. Healthcare organizations set technical standards to measure system uptime and data security.
Good SLAs must include “clearly articulated expectations, deliverables and desired outcomes” with detailed assessment measures and consequences. Two key points need attention: cure periods should match the problem’s size, and ongoing issues need permanent fixes even if vendors fix single incidents quickly.
SLAs should work as living blueprints for vendor relationships rather than forgotten paperwork. Both fields benefit when teams regularly check these agreements to “motivate vendors to drive performance to a new level”.
Conclusion
RFP Risk management strategies in construction sites and healthcare data protection reveal distinctly different approaches to equally important concerns. Physical risks need immediate action through safety protocols. Digital vulnerabilities need technical safeguards to protect sensitive patient information. These domains share core principles even with their unique challenges.
Each domain needs specific assessment frameworks that fit their unique operational environments. Construction projects work well with methodologies like INSHT and FINE. Healthcare organizations use specialized tools that cover both physical safety and data security. These strategies take shape from regulatory frameworks – OSHA guides construction safety protocols while HIPAA sets strict requirements to protect patient information.
Risk reduction reflects what each domain values most. Construction safety relies on controlling site access, maintaining equipment properly, and planning for environmental hazards. Healthcare data protection depends on encryption, role-based access controls, and detailed audit trails in electronic health record systems.
RFP Risk Management processes should include criteria that properly review vendor capabilities in each domain. Construction bid scoring should look at safety protocols. Healthcare proposals need careful examination of data security measures. Note that picking partners who have shown strong risk management skills helps protect both physical safety and data privacy.
Looking at these domains side by side teaches valuable lessons about risk management. Incident response planning, security awareness training, and vendor accountability work in both physical and digital environments. Organizations should adopt these common best practices while keeping domain-specific approaches to handle unique threats.
RFP Risk management boils down to protecting what matters most – workers on construction sites or patients whose sensitive information moves through healthcare systems. Understanding these parallel risk landscapes helps create strong evaluation criteria in any industry. This creates safer environments in both physical and digital worlds.
Check out these articles to learn more about success in RFP’s:
Key Takeaways
RFP Risk management strategies vary dramatically between physical construction sites and digital healthcare environments, yet both domains share fundamental principles that can strengthen organizational resilience across industries.
• Domain-specific assessment frameworks are essential – Construction uses methodologies like INSHT and FINE, while healthcare requires specialized tools addressing both physical safety and data security vulnerabilities.
• Regulatory compliance shapes risk strategies differently – OSHA mandates guide construction safety with penalties up to $161,323 per violation, while HIPAA requires strict patient data protection with breach costs averaging $7.13 million.
• Physical risks demand immediate visible responses, digital risks often remain hidden – Construction accidents cause immediate harm requiring site access controls and safety protocols, while healthcare data breaches can go undetected until significant damage occurs.
• RFP evaluation criteria must reflect domain-specific capabilities – Construction bids should be scored on safety protocols and equipment failure planning, while healthcare proposals require rigorous assessment of encryption, access controls, and audit trail systems.
• Cross-domain lessons strengthen overall resilience – Incident response planning, security awareness training, and vendor accountability through SLAs apply effectively across both physical and digital environments.
Effective risk management ultimately protects what matters most—whether safeguarding workers on construction sites or securing sensitive patient information in healthcare systems. Organizations benefit from understanding these parallel risk universes to develop comprehensive protection strategies regardless of industry.
FAQs
Q1. What are the key risk management strategies in project management? The five critical steps in project risk management are identification, assessment, treatment, monitoring, and reporting. This process involves recognizing potential risks, evaluating their severity, implementing mitigation measures, continuously tracking risks, and communicating updates to stakeholders.
Q2. How does risk management differ between construction sites and healthcare data protection? Construction sites focus on immediate physical hazards like falls and equipment failures, requiring on-site safety protocols. Healthcare data protection addresses digital risks like data breaches and unauthorized access, necessitating encryption and access controls. While the specific risks differ, both domains require thorough assessment, mitigation strategies, and regulatory compliance.
Q3. What role do RFPs play in risk management? RFPs (Requests for Proposals) are crucial in risk management as they allow organizations to evaluate potential vendors’ risk mitigation capabilities. In construction, RFPs assess safety protocols and equipment failure planning. For healthcare, RFPs examine data security measures like encryption and audit trails. Effective RFPs help select partners who can manage domain-specific risks.
Q4. How can organizations improve incident response across physical and digital domains? Organizations can enhance incident response by developing comprehensive plans that assign clear roles and responsibilities, conducting regular simulation exercises, and holding blameless retrospective meetings to learn from incidents. These practices apply to both construction site accidents and data breaches, helping teams respond more effectively to crises.
Q5. What are some shared best practices for risk reduction in construction and healthcare? Both domains benefit from robust training and awareness programs that address human factors in risk management. Additionally, implementing strong vendor accountability measures through well-crafted Service Level Agreements (SLAs) is crucial. Regular review and updates of these practices ensure ongoing risk reduction in both physical and digital environments.
